Achieving CIS Security Controls 1 & 2 in Asset Management
How do CIS Controls 1 and 2 play a part in the context of asset management? To start, CIS Controls are a set of best practices that help organizations reduce their attack surface and maintain compliance with industry regulations such as NIST 800-53, ISO 27001, GLBA, HIPAA/HITECH Act, and Sarbanes-Oxley.
These controls provide the foundation for an effective cybersecurity program by addressing key IT security risks like:
- Vulnerabilities in application code
- Insufficient access control
- Improper use of privileges
- Data loss or theft
- Sabotage or espionage
- Denial of service attacks
- Destruction or disruption to infrastructure
When your organization implements these controls, you can identify vulnerabilities before they're exploited and protect sensitive information from attackers who might try to steal it.
What is CIS in Asset Management?
CIS is the acronym for the Center for Internet Security, an independent organization that focuses on creating standards for security among connected devices. They've established best practices for organizations to help simplify managing IT assets and infrastructure.
The benefits of achieving CIS Security Controls 1 & 2 include increased protection for company assets. CIS compliance also improves IT service levels, quality assurance, and accountability. CIS helps with developing comprehensive business continuity plans that help with disaster recovery.
The CIS security controls allow the organization to better understand risks and threats to critical assets.
You may evaluate the controls by looking at risk assessment, cost analysis, and level of effort analysis.
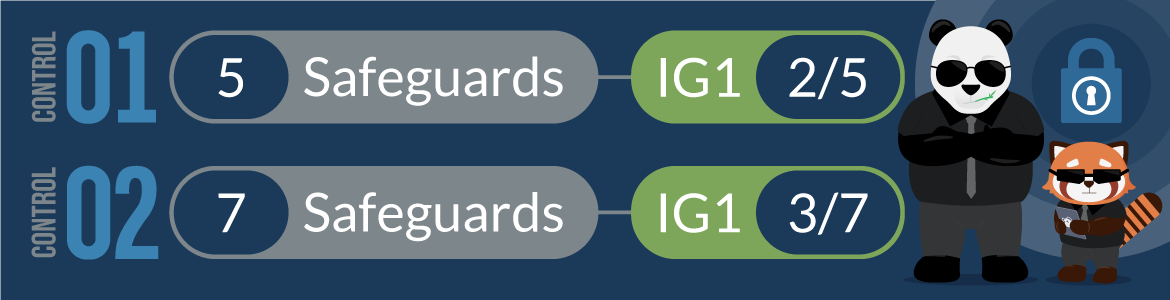
There are 18 total CIS controls, which fall into three core implementation groups. We'll briefly address the three implementation groups. Still, in this article, we'll only explore the first two CIS controls— Inventory and Control of Enterprise Assets and Inventory and Control of Software Assets.
CIS Implementation Groups
CIS implementation groups are recommended guidance parameters for prioritizing the implementation of CIS critical security controls. Each of the three implementation groups builds on the previous and includes multiple individual controls.
CIS Controls Implementation Group 1
Implementation Group 1 (or IG1) could be considered the 'essentials' of cybersecurity. It includes basics like cyber hygiene and helps companies achieve the minimum standards of information security, applicable to nearly all enterprises at every level. The Center for Internet Security describes it as the 'on-ramp' to the CIS controls. It consists of 56 cyber defense Safeguards designed to provide the most basic level of defense against the most common types of attacks.
Companies that are at the CIS Control Implementation Group 1 level tend to be small to medium-sized businesses. They have limited budgets and resources but are more likely to be targeted by opportunistic attacks. These companies need a strong foundation of security practices that can help them move forward in their cybersecurity journey.
CIS Controls Implementation Group 2
Implementation Group 2 (or IG2) is the next step up from implementation group one and includes additional controls beyond what's included in implementation group one. IG2 is the stage where most organizations want to be, as it offers a good balance between security and costs. The Center for Internet Security recommends the implementation of Group II as an intermediary step before implementing controls in Implementation Group III.
Implementation Group II includes 24 Safeguards that address some of the more advanced cyber threats out there, like zero-day exploits and malware. These controls help companies detect malicious activity on their networks so they can respond quickly to these types of threats, but also give them some more protection against commodity attacks that might be targeted at basic Windows or Linux vulnerabilities—the kind you'll find in the implementation group one list of cyber defense measures.
CIS Controls Implementation Group 3
Implementation Group III (or IG3) is the highest implementation stage and includes additional controls beyond what's included in Implementation Groups I & II. It's designed for companies that are especially security conscious or may be subject to industry-specific compliance requirements like PCI DSS or HIPAA. These Safeguards include higher-level protections than those required by CIS implementation groups one and two.
By implementing all three levels of protection outlined above, organizations can help protect against current cyber threats while also preparing themselves for even more advanced attacks down the road.
CIS Control 1: Inventory and Control of Enterprise Assets
This control focuses on creating an inventory of all hardware assets that access a network to determine which devices are authorized for use by employees or other third parties who require remote access.
It also provides additional protection against stolen equipment being used as an attack vector when unauthorized individuals have physical access to these resources. In this case, organizations can identify compromised systems before they've been impacted or damaged through malware attacks like ransomware.
How to Achieve CIS Control 1
This control includes several detailed requirements, such as:
- Creating an accurate inventory of all hardware assets attached to the network
- Authorizing each device for connection and use by employees or other authorized parties only
- Ensuring unauthorized devices are not connected to enterprise resources and services at any time. You can achieve this through technical controls like firewalls and proxies, which prevent unwanted access from outside networks.
These protections should also detect abnormal traffic, including encrypted communication channels that could indicate malware activity. The next step is encrypting data in motion across these communications links so they cannot be intercepted during transmission between different points on the network (like when entering via VPN.) Data at rest encryption deals with storage protection instead of transit security—preventing unauthorized access to data when it is sitting on a server.
Compiling a list of all company-owned equipment in an asset management software like Asset Panda can help companies accomplish the first part of CIS Control 1, putting them on the path to becoming an IG1 organization.
CIS Control 2: Inventory and Control of Software Assets
In CIS Control 2, your company has to have an inventory and control of software assets. This means that you need to know what software licenses you have, how many computers are using these software licenses, and if there are any discrepancies between what is in your inventory and what is actually loaded on the computers.
For example, if your inventory says that there are ten licenses for software X, but only eight copies of this software are installed on the computers, then you have two unaccounted-for copies of this software license. If you find these copies later by chance, ensure you account for them in your software asset management system.
A solution like Asset Panda can help track what software is associated with the devices your company owns. This can also help identify when new licenses are needed, when you're overpaying for software, and how to ensure that all of your software users have the support they need.
The following requirement of this control is to ensure that only authorized users can access or use your software. This means the user has a valid license for the copy they are using, and no other unauthorized copies are being used either on their computer or elsewhere in your organization.
For example, suppose you have an agreement with another company that allows employees at both companies to share licenses between them. In that case, all parties involved must be documented properly so it doesn't appear as though additional people have unauthorized access to these resources when, in reality, they don't.
You'll also want to ensure accurate records surrounding who is allowed to use which programs and what devices (like laptops) those individuals will typically use each day while working remotely from different locations around the world. Tracking that equipment with an IT asset tracking tool can provide you with a better understanding of who has what and where they're using it.
How to Achieve CIS Control 2
To achieve CIS Control 2, it would be wise to ensure that all licenses currently installed on computers are appropriately accounted for in the system.
Additionally, you need to make sure that all software installed on your network is documented and known by IT staff. This includes identifying each piece of software along with its version number through asset inventory audits. If there are any discrepancies between what you have recorded versus what is actually installed, then this needs to be corrected immediately (i.e., if only one computer uses a particular license, but it was not initially recorded).
You must have clear instructions about how new equipment will be added to the list of existing equipment so that you can properly assign these licenses to these new machines before they go into use. Otherwise, you risk having additional licenses on the books you do not know about, which can cause severe problems in your organization.
Conclusion
Achieving CIS security controls 1 and 2 in asset management is a must for any company that needs to ensure the safety of their data. If you need help figuring out where to start, don't worry!
From creating an accurate inventory of all hardware assets attached to the network to authorizing each device for connection and use by employees or other authorized parties only— and everything in between— Asset Panda can help your organization achieve CIS Security levels based on your unique needs and security goals.
Request your demo today for free access to Asset Panda for 14 days (no card required).
Related News & Press

Learn more from an Asset Panda expert
Get a FREE consultation with an asset tracking expert to find out how you can transform your asset tracking.
Contact our Sales Team at (888) 928-6112